Entendendo o PCI DSS: Porque os padrões promovidos pelo Payment Card Industry Council são bem mais do que um simples Snake Oil

Este artigo do Eduardo Neves explica muito sobre o PCI-DSS. Imperdível para quem está envolvido no assunto.
Ideias, Insights, Links, Viagens e Pensamentos diversos sobre Segurança da Informação e otras cositas mais...

Este artigo do Eduardo Neves explica muito sobre o PCI-DSS. Imperdível para quem está envolvido no assunto.
Our good friend Sascha from Netbook News recently got to poke his nose around Kingston's production lines, specifically the factory where USB thumb drives are put together. Luckily for us, after Sascha had donned his natty cap and other dust-busting gear, he picked up his video camera and took it in with him.
The biggest surprise is how office-like this seems. If you expect the factory resemble those which churn out cars or wash returned milk bottles, you'll be disappointed. The machines which do the work here are small and quiet, more like photocopiers than giant, Transformer-like welding-bots. In fact, we're reminded of nothing so much as a high-street print bureau. Which is, given the nature of circuit production, not far from the truth. Bonus: Just over halfway in, the memory card in the video camera gets almost full — inside a memory-making factory!
How's a USB Is Made? Trip to the Kingston Production Plant [Netbook News. Thanks, Sascha!]
Labels: hardware
Muito divertido, vale a leitura....
 If you think about it, table manners are just one of the ways The Man has got us under his thumb. Separate forks for salad, fish, oyster and dinner? It's oppression, I tell you.
If you think about it, table manners are just one of the ways The Man has got us under his thumb. Separate forks for salad, fish, oyster and dinner? It's oppression, I tell you.
Our BFF BuzzFeed is revolting against some of the stupidest table manners today and have provided means for us regular Joes to resist being civilized:
1. Multiple Forks
Oppressive rule: You sit down at a fancy restaurant and are immediately faced with a vast array of forks.Resistance solution: Side-step the utensils. God gave you hands for a reason.
2. Eating Soup With A Spoon
Oppressive rule: Despite the fact that soup is a liquid, we're forced to ladle in out in painfully small increments, always with the threat of spillage.Resistance solution: Use a straw if it's thin broth; lift the bowl and DRINK DIRECTLY FROM THE BOWL if it's anything hearty.
Miss Manners is surely horrified: Link - Thanks Matt!
Labels: fun

An ambitious group of hardware hackers have taken the fundamental building blocks of computing and turned them inside out in an attempt to make PCs significantly more efficient.
The group has created a motherboard prototype that uses separate modules, each of which has its own processor, memory and storage. Each square cell in this design serves as a mini-motherboard and network node; the cells can allocate power and decide to accept or reject incoming transmissions and programs independently. Together, they form a networked cluster with significantly greater power than the individual modules.
The design, called the Illuminato X Machina, is vastly different from the separate processor,memory and storage components that govern computers today.
"We are taking everything that goes into motherboard now and chopping it up," says David Ackley, associate professor of computer science at the University of New Mexico and one of the contributors to the project. "We have a CPU, RAM, data storage and serial ports for connectivity on every two square inches."
A modular architecture designed for parallel and distributed processing could help take computing to the next level, say its designers. Instead of having an entire system crash if a component experiences a fatal error, failure of a single cell can still leave the rest of the system operational. It also has the potential to change computing by ushering in machines that draw very little power.
"We are at a point where each computer processor maxes out at 3Ghz (clock speed) so you have to add more cores, but you are still sharing the resource within the system," says Justin Huynh, one of the key members of the project. "Adding cores the way we are doing now will last about a decade."
Huynh and his team are no strangers to experimenting with new ideas. Earlier this year, Huynh and his partner Matt Stack created the Open Source Hardware Bank, a peer-to-peer borrowing and lending club that funds open source hardware projects. Stack first started working on the X Machina idea about 10 months ago.
Computing today is based on the von Neumann architecture: a central processor, and separate memory and data storage. But that design poses a significant problem known as the von Neumann bottleneck. Though processors can get faster, the connection between the memory and the processor can get overloaded.That limits the speed of the computer to the pace at which it can transfer data between the two.
"A von Neumann machine is like the centrally planned economy, whereas the modular, bottom up, interconnected approach would be more capitalist," says Ackley."There are advantages to a centrally planned structure but eventually it will run into great inefficiencies."
 By creating modules, Huynh and his group hope to bring a more parallel and distributed architecture. Cluster-based systems aren't new. They have been used in high end computing extensively. But with the Illuminato X Machina they hope to extend the idea to a larger community of general PC users.
By creating modules, Huynh and his group hope to bring a more parallel and distributed architecture. Cluster-based systems aren't new. They have been used in high end computing extensively. But with the Illuminato X Machina they hope to extend the idea to a larger community of general PC users.
"The way to think of this is that it is a system with a series of bacteria working together instead of a complex single cell amoeba," says JP Norair, architect of Dash 7, a new wireless and data standard. An electrical and computer engineering graduate from Princeton University, Norair has studied modular architecture extensively.
Each X Machina module has a 72 MHz processor (currently an ARM chip), a solid state drive of 16KB and 128KB of storage in an EEPROM (electrically erasable programmable read-0nly memory) chip. There's also an LED for display output and a button for user interaction.
Every module has four edges, and each edge can connect to its neighbors. It doesn't have sockets, standardized interconnects or a proprietary bus. Instead, the system uses a reversible connector. It's smart enough to know if it is plugged into a neighbor and can establish the correct power and signal wires to exchange power and information, says Mike Gionfriddo, one of the designers on the project.
The X Machina has software-controlled switches to gate the power moving through the system on the fly and a 'jumping gene' ability, which means executable code can flow directly from one module to another without always involving a PC-based program downloader.
Each Illuminato X Machina node also has a custom boot loader software that allows it to be programmed and reprogrammed by its neighbors, even as the overall system continues to run, explains Huynh. The X Machina creators hope to tie into the ardent Arduino community. Many simple Arduino sketches will run on the X Machina with no source code changes, they say.
Still there are many details that need to be worked out. Huynh and his group haven't yet benchmarked the system against traditional PCs to establish exactly how the two compare in terms of power consumption and speeds. The lack of benchmarking also means that they have no data yet on how the computing power of an X Machina array compares to a PC with an Intel Core 2 Duo chip.
Programs and applications have also yet to be written for the X Machina to show whether it can be an effective computing system for the kind of tasks most users perform. To answer some of these questions, Ackley plans to introduce the Illuminato X Machina to his class at the University of New Mexico later this month. Ackley hopes students of computer science will help understand how traditional computer programming concepts can be adapted to this new structure.
So far, just the first few steps towards this idea have been taken, says Huynh.
Norair agrees. "If they can successfully get half the power of an Intel chip with a cluster of microcontrollers, it will be a great success," he says, "because the power consumption can be so low on these clusters and they have a level of robustness we haven't seen yet."
See the video to hear David Ackley talk about programming the Illuminato X Machina.
Programming the Illuminato X Machina from Chris Ladden on Vimeo.
Photo: Illuminato X Machina/Justin Huynh
via Nettuts+ by Vasili on 8/10/09
Regular expressions are a language of their own. When you learn a new programming language, they're this little sub-language that makes no sense at first glance. Many times you have to read another tutorial, article, or book just to understand the "simple" pattern described. Today, we'll review eight regular expressions that you should know for your next coding project.
This is what Wikipedia has to say about them:
In computing, regular expressions provide a concise and flexible means for identifying strings of text of interest, such as particular characters, words, or patterns of characters. Regular expressions (abbreviated as regex or regexp, with plural forms regexes, regexps, or regexen) are written in a formal language that can be interpreted by a regular expression processor, a program that either serves as a parser generator or examines text and identifies parts that match the provided specification.
Now, that doesn't really tell me much about the actual patterns. The regexes I'll be going over today contains characters such as \w, \s, \1, and many others that represent something totally different from what they look like.
If you'd like to learn a little about regular expressions before you continue reading this article, I'd suggest watching the Regular Expressions for Dummies screencast series.
The eight regular expressions we'll be going over today will allow you to match a(n): username, password, email, hex value (like #fff or #000), slug, URL, IP address, and an HTML tag. As the list goes down, the regular expressions get more and more confusing. The pictures for each regex in the beginning are easy to follow, but the last four are more easily understood by reading the explanation.
The key thing to remember about regular expressions is that they are almost read forwards and backwards at the same time. This sentence will make more sense when we talk about matching HTML tags.
Note: The delimiters used in the regular expressions are forward slashes, "/". Each pattern begins and ends with a delimiter. If a forward slash appears in a regex, we must escape it with a backslash: "\/".
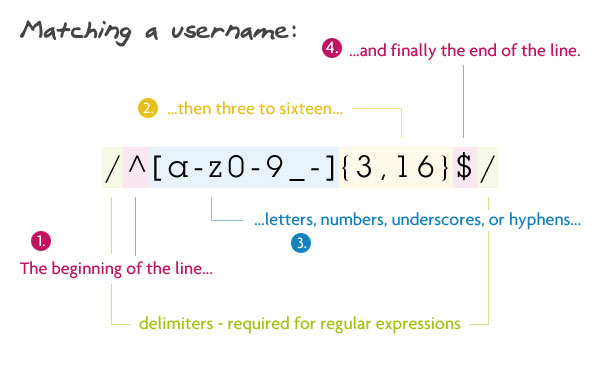
/^[a-z0-9_-]{3,16}$/ We begin by telling the parser to find the beginning of the string (^), followed by any lowercase letter (a-z), number (0-9), an underscore, or a hyphen. Next, {3,16} makes sure that are at least 3 of those characters, but no more than 16. Finally, we want the end of the string ($).
my-us3r_n4m3
th1s1s-wayt00_l0ngt0beausername (too long)

/^[a-z0-9_-]{6,18}$/ Matching a password is very similar to matching a username. The only difference is that instead of 3 to 16 letters, numbers, underscores, or hyphens, we want 6 to 18 of them ({6,18}).
myp4ssw0rd
mypa$$w0rd (contains a dollar sign)

/^#?([a-f0-9]{6}|[a-f0-9]{3})$/ We begin by telling the parser to find the beginning of the string (^). Next, a number sign is optional because it is followed a question mark. The question mark tells the parser that the preceding character — in this case a number sign — is optional, but to be "greedy" and capture it if it's there. Next, inside the first group (first group of parentheses), we can have two different situations. The first is any lowercase letter between a and f or a number six times. The vertical bar tells us that we can also have three lowercase letters between a and f or numbers instead. Finally, we want the end of the string ($).
The reason that I put the six character before is that parser will capture a hex value like #ffffff. If I had reversed it so that the three characters came first, the parser would only pick up #fff and not the other three f's.
#a3c113
#4d82h4 (contains the letter h)

/^[a-z0-9-]+$/
You will be using this regex if you ever have to work with mod_rewrite and pretty URL's. We begin by telling the parser to find the beginning of the string (^), followed by one or more (the plus sign) letters, numbers, or hyphens. Finally, we want the end of the string ($).
my-title-here
my_title_here (contains underscores)

/^([a-z0-9_\.-]+)@([\da-z\.-]+)\.([a-z\.]{2,6})$/ We begin by telling the parser to find the beginning of the string (^). Inside the first group, we match one or more lowercase letters, numbers, underscores, dots, or hyphens. I have escaped the dot because a non-escaped dot means any character. Directly after that, there must be an at sign. Next is the domain name which must be: one or more lowercase letters, numbers, underscores, dots, or hyphens. Then another (escaped) dot, with the extension being two to six letters or dots. I have 2 to 6 because of the country specific TLD's (.ny.us or .co.uk). Finally, we want the end of the string ($).
john@doe.com
john@doe.something (TLD is too long)

/^(https?:\/\/)?([\da-z\.-]+)\.([a-z\.]{2,6})([\/\w \.-]*)*\/?$/ This regex is almost like taking the ending part of the above regex, slapping it between "http://" and some file structure at the end. It sounds a lot simpler than it really is. To start off, we search for the beginning of the line with the caret.
The first capturing group is all option. It allows the URL to begin with "http://", "https://", or neither of them. I have a question mark after the s to allow URL's that have http or https. In order to make this entire group optional, I just added a question mark to the end of it.
Next is the domain name: one or more numbers, letters, dots, or hypens followed by another dot then two to six letters or dots. The following section is the optional files and directories. Inside the group, we want to match any number of forward slashes, letters, numbers, underscores, spaces, dots, or hyphens. Then we say that this group can be matched as many times as we want. Pretty much this allows multiple directories to be matched along with a file at the end. I have used the star instead of the question mark because the star says zero or more, not zero or one. If a question mark was to be used there, only one file/directory would be able to be matched.
Then a trailing slash is matched, but it can be optional. Finally we end with the end of the line.
http://net.tutsplus.com/about
http://google.com/some/file!.html (contains an exclamation point)

/^(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)$/ Now, I'm not going to lie, I didn't write this regex; I got it from here. Now, that doesn't mean that I can't rip it apart character for character.
The first capture group really isn't a captured group because
?:
was placed inside which tells the parser to not capture this group (more on this in the last regex). We also want this non-captured group to be repeated three times — the {3} at the end of the group. This group contains another group, a subgroup, and a literal dot. The parser looks for a match in the subgroup then a dot to move on.
The subgroup is also another non-capture group. It's just a bunch of character sets (things inside brackets): the string "25″ followed by a number between 0 and 5; or the string "2″ and a number between 0 and 4 and any number; or an optional zero or one followed by two numbers, with the second being optional.
After we match three of those, it's onto the next non-capturing group. This one wants: the string "25″ followed by a number between 0 and 5; or the string "2″ with a number between 0 and 4 and another number at the end; or an optional zero or one followed by two numbers, with the second being optional.
We end this confusing regex with the end of the string.
73.60.124.136 (no, that is not my IP address ![]() )
)
256.60.124.136 (the first group must be "25″ and a number between zero and five)

/^<([a-z]+)([^<]+)*(?:>(.*)<\/\1>|\s+\/>)$/
One of the more useful regexes on the list. It matches any HTML tag with the content inside. As usually, we begin with the start of the line.
First comes the tag's name. It must be one or more letters long. This is the first capture group, it comes in handy when we have to grab the closing tag. The next thing are the tag's attributes. This is any character but a greater than sign (>). Since this is optional, but I want to match more than one character, the star is used. The plus sign makes up the attribute and value, and the star says as many attributes as you want.
Next comes the third non-capture group. Inside, it will contain either a greater than sign, some content, and a closing tag; or some spaces, a forward slash, and a greater than sign. The first option looks for a greater than sign followed by any number of characters, and the closing tag. \1 is used which represents the content that was captured in the first capturing group. In this case it was the tag's name. Now, if that couldn't be matched we want to look for a self closing tag (like an img, br, or hr tag). This needs to have one or more spaces followed by "/>".
The regex is ended with the end of the line.
<a href="http://net.tutsplus.com/">Nettuts+</a>
<img src="img.jpg" alt="My image>" /> (attributes can't contain greater than signs)
I hope that you have grasped the ideas behind regular expressions a little bit better. Hopefully you'll be using these regexes in future projects! Many times you won't need to decipher a regex character by character, but sometimes if you do this it helps you learn. Just remember, don't be afraid of regular expressions, they might not seem it, but they make your life a lot easier. Just try and pull out a tag's name from a string without regular expressions! ![]()
Labels: programação
 If your note-taking skills are suffering from summertime rigor mortis, now's as good a time as any to throw a new technique into the mix. Let's take a look at some new and old tools for improving your ballpoint repertoire.
If your note-taking skills are suffering from summertime rigor mortis, now's as good a time as any to throw a new technique into the mix. Let's take a look at some new and old tools for improving your ballpoint repertoire.
Photo by JasonRogersFooDogGiraffeBee.
This oldie is a highly-regarded, very common system that makes it especially easier to retain information. By reviewing things as you go, you might even get away with less studying.
Divide your page into two columns. The left one (which could also just be the back of the previous page in your notebook) is narrower. You're going to jot larger ideas in this column: the 5-dollar-words and big bullet points. In the right column, you're going to take down as much information as possible. The right column is allowed to be messy, have pictures and tables—it's not necessarily organized. To some students, it's just regular notes. But as you go, record the main corresponding idea in the left column.
Every so often, cover the detailed notes on the right and just examine the main points and new vocab. See how much you can recite and explain in your own words. Then remove your hand and see how you did. Depending on the teacher, you might do this during lulls in the discussion or after class.
Some versions of the Cornell system leave the last few lines on each page for summarizing the whole page. Since what's on a given page doesn't necessarily group together nicely, I don't recommend doing it. But summarizing can help you with wading through piles of pages when studying time comes.
For a more in-depth look at the Cornell method, take a look at our previous guide to taking study-worthy lecture notes.
It's tough to enter a classroom with colored pencils and still expect your fellow students to take you seriously. But unless you try it, you'll never know if it works better for you. Forget the status-quo and try something visual. Color-code with different pens, pencils, and highlighters. You might not have seen a web-style map of ideas since elementary school, but mind-mapping is hailed as quite an efficient way to group data. It needn't even be a rigid classification system—anything is better than doodling in the margins.
For how tech-savvy our generation is, I still see surprisingly few laptops in classrooms. Try it out a few times and see if you like it. Particularly, if you're the type who outlines, computers let you go back and organize information on-the-fly. Laptops also let you and your classmates AIM with real-time questions about the opposite sex the lecture. There are also programs made just for taking notes, sharing them, organizing them, etc. Wikipedia has a great table that compares them all, or you can take a look at Lifehacker reader's favorite note-taking tools.
On the other hand, if you already use a laptop, try the pen-and-paper route again. Let loose a bit and see how that goes. Try scribbling out mistakes and drawing arrows everywhere. Or try one of the visual techniques above, most of which are difficult on a computer.
Notes are probably the only place in the classroom where internet slang is commendable. Trying some new shorthand is a really geeky way to slightly tweak your engravings and get you amped about taking notes again. Here are a few resources to get you started:
A Guide to Alternative Handwriting and Shorthand Systems
Shorthand Shorthand Shorthand
My favorite method is called Teeline—anyone can look at this one and learn a few things. It's mostly based around removing unimportant letters and making complex letters easier to write quickly.
Instead of converting entirely to shorthand, you might try translating just some of your most-frequently used words into a shorthand "language" that takes less time to write.
If you're taking notes on the computer, supercharge your repetitive typing with tools like our very own text-replacement application Texter (Windows) or TextExpander (Mac).
Oh goodness! Don't take notes? How controversial!
Well, it couldn't hurt to relax every once in a while. Especially in small classes and seminar situations, staying engaged through discussion and questions might do you better than scribbling every word.
Here's another way to avoid taking notes: Record your lectures. Digital recorders can capture hours of audio. Sit back and just listen. After class, you can play it back at double-speed and take notes in half the time. Take that, engineers!
The school-bound productivity nuts at weblog HackCollege will be joining us all week to offer their perspective on making the most of your Back to School regimen.
Labels: produtividade
Abandoned buildings have become one of my favorite subjects to photograph. Over time, I have collected a handful of useful tips to get the most out of shooting in these environments.
The single most important tip I can provide anyone planning on visiting an abandoned building is to bring a flashlight. Most of these locations are without electricity and will have limited natural light. As such, you'll need a flashlight to help navigate the dark rooms and corridors that you will encounter.
Beyond its more obvious application, a flashlight can also provide an interesting source of off-camera lighting. I have a small LED flashlight that I carry on my camera bag and it is often used to light up an area of a room during a long exposure shot. While a strobe can certainly be effective for many of these situations, a flashlight allows for a high degree of precision with the light. You can directly control exactly what is lit and for how long. A flashlight can also add an element of movement to the lighting that will result in an unusual combination of shadows that a flash otherwise may not.
It takes some practice to get a feel for how much light is enough, but with some work the results can be very satisfying.
Because of the aforementioned lighting conditions, it goes without saying that you will need a tripod. More than half of the photos I take at these locales are shot on a tripod with a long exposure of anywhere from a couple of seconds to as much as 20 or 30 seconds.
For those instances when I don't have my camera on a tripod, image stabilization and fast lenses help as well. My favorite lens is a 17-50mm f/2.8 paired with my camera's in-body stabilized sensor. Wide open, I can usually get a relatively sharp image at 1/10th of a second. More often than not though, the best results will come from shooting on a tripod.
I am not one who believes all serious photographers should shoot in manual 100% of the time. There are plenty of instances where I am confident that the camera will properly meter the lighting and autopilot mode is fine. Unfortunately, that tactic will not work in most abandoned buildings.
Because of the extreme lighting conditions of these spaces, you'll need to control all aspects of the shot. In the photo shown here, for example, I needed to control the aperture (I wanted this fairly sharp from front to back) and I needed to control the shutter speed to ensure proper lighting. So, in this case I shot for 30 seconds at f/8. This particular image is also another example of the flashlight technique described above… I used it to highlight and bring attention to the chairs while leaving the walls to be lit by the little bit of light coming from the window.
A wide angle lens can really add to the sense of emptiness and foreboding in these buildings. The photo shown below was taken by a friend of mine with a 10-22mm lens at 10mm. Having something that can go wide in the small areas you'll be photographing can be a huge benefit.
Use creative angles and perspectives to play up the natural character of the buildings. Get your camera low to the ground and shoot upwards to emphasize the vastness of a room, or shoot an angle to heighten the sense of disorientation. As a photographer you are telling the story of the place you are in and even a subtle shift of the camera's perspective can make a huge impact on the mood of the photo.
While it is easy to get caught up in the architecture, try to also pay attention to the discarded items and details in the area as well. Chairs, books, phones and other remnants from days gone by can provide a powerful centerpiece to the image. Focusing on a single object can also act as an anchor in an otherwise chaotic environment.
My final tip is for you to be careful while exploring these buildings. No photograph is worth endangering yourself, so take extreme precaution whenever you enter an unfamiliar location. Be safe and happy shooting! Chris Folsom is a hobbyist photographer who spends much of his time photographing buildings that are no longer in use. You can view his site at studiotempura.com or see more of his photos at Flickr. His photos have been published on numerous websites and newspapers.
Chris Folsom is a hobbyist photographer who spends much of his time photographing buildings that are no longer in use. You can view his site at studiotempura.com or see more of his photos at Flickr. His photos have been published on numerous websites and newspapers.
Post from: Digital Photography School - Photography Tips.
Labels: fotografia
If you checked out the PSU calculator we shared with you and wished it had a more detailed selection process for really granular and precise control, you'll definitely want to check out the eXtreme Power Supply Calculator.
The calculator in the link above is great for a quick estimate, but what if you want to be able to run a more detailed calculation before purchasing your new PSU? The eXtreme PSU calculator pulls from a very detailed database of parts to give you a more accurate estimate. During our testing we were able to select the exact CPU and graphics card, for example, that our test system was running.
There are dozens of variables you can set within the Lite version of the calculator, for even more options there is a $1.99 premium version of the calculator with even more settings for your calculating pleasure. Thanks Erik!
Labels: hardware
O que o Youtube criou, meu Deus?
Sério. Qual o motivo de um cara treinar resolver um cubo mágico (ou dois!) enquanto toca Guitar Hero World Tour no Expert? "Melhorar a coordenação e a musculatura do cotovelo", você pode apontar. "É um exercício que os psicólogos passam hoje para curar crianças com déficit de atenção", uma prima da sua amiga que estuda psicologia dá o pitaco.
Mas não. A ideia é só colocar a façanha no Youtube e ver quantos % falam "você precisa fazer sexo" (mesmo que ele tenha aparentemente 16 anos), quantos escrevem "AWESOME" e quantos duvidam de alguma das coisas. "Foi tudo photoshopado".
Ah, sim, como você pode ver pela terrível execução de Mr. Crowley, do Ozzy, a especialidade do JRefleX93 é resolver Cubos Mágicos. O recorde dele no tradicional 3x3 é 16.44 segundos. Um pouco menos que o tempo que eu levo para comer um hamburguer do McDonald's. Como fazer isso sem estudar meticulosamente o cubo (perceba que ele olha pouco para o negócio): é "só" usar o Método Fridrich. Moleza. [Via Continue]

"I had this dream from childhood of not needing to climb mountains anymore. I wanted to go to school in my own flying machine."
This was the childhood dream of Wu Zhongyuan, of China's Henan province. It is also, quite likely, a childhood dream of most you, dear Gadget Lab readers. Unlike you, though, Zhongyuan actually did something about it. He built his own helicopter.
The device, which likely breaks almost every airspace and safety law simultaneously, is made from steel scaffold, has blades cut from Elm and is powered by an old motorcycle engine. Zhongyuan says that the 'copter, which took three months and around $1600 to build, can soar to 800 meters (2600 feet). We're not sure if it can even get airborne, though, as currently the machine is grounded by Chinese authorities.
How did he come up with his ramshackle design? The internet, of course. "I didn't have a design. The only source for me to get relevant knowledge was surfing the internet via my mobile phone," he said to news site Ananova. We love it. A personal helicopter is a fantastic project, and we wish Zhongyuan luck getting it off the ground. Of course, we'd never go near the thing. Imagine being half a mile up and when the engine cuts out on you. No thanks.
Farmer's home-made helicopter [Ananova via DVICE]
Chinese farmer builds a working wooden helicopter [Auto Motto]